
Bitcoin, Ethereum, and Solana all rely on elliptic-curve signatures (i.e., each wallet is a pair of private and public keys). The hidden private key is used to create an authentication signature, and the public key (derived from the private key) is used for verification of that signature. Today, it is computationally impossible for a classical computer to reverse engineer the private key from the public key.
In theory, however, a sufficiently advanced quantum computer could break this assumption.
If quantum computing achieves this before widespread quantum protections are in place across the crypto industry, actors with access to quantum machines could eventually steal funds from anyone participating in today’s crypto systems. To be clear, a quantum breakthrough would impact many industries beyond crypto—most notably defense, national security, critical infrastructure, and identity systems—which is why NIST and national security agencies have been actively developing post-quantum cryptographic standards and migration plans.
Although the widespread public narrative surrounding this topic stresses urgency and fear, the threat is not imminent. Actual Q-day—the moment when quantum computers can break today’s public-key cryptography—remains decades away, not years.
Breaking elliptic-curve cryptography (ECC) requires thousands of logical qubits, which would require millions of physical qubits with error correction. Today’s largest machines are roughly 6,100 physical qubits, meaning the industry is still multiple technological leaps away (approximately 150x scaling).
Of course, planning for migration must begin before the threat properly materializes, and in that regard, Solana is ahead of the curve with a temporary mitigation in place: the Winternitz Vault. This is a smart contract that uses hash-based and quantum-resistant signatures. With it, users generate a post-quantum, offchain keypair, and then deposit SOL into the vault for long-term quantum-safe storage.
Developers can already build quantum-resistant applications using Winternitz signatures and Blueshift is turning this into a consumer-facing product that is expected soon.
This protects long-term holders in the case that quantum development unexpectedly accelerates and Q-day arrives earlier than expected. While users protect their funds in that scenario, long-term solutions can be worked on and implemented.
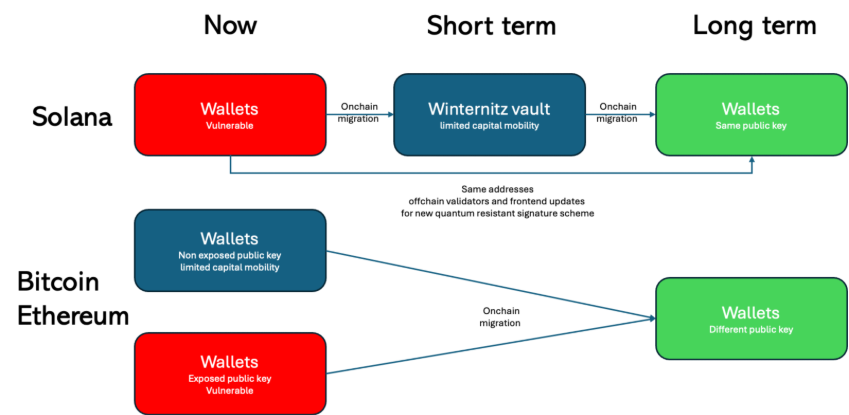
It is, however, important to note that the Winternitz signature scheme explicitly requires a new address after each transaction, which is a major UX and security constraint—the reason it is considered a temporary solution to the quantum issue at hand.
Path To A Fully Post-Quantum Solana
A complete Solana migration to post-quantum blockchain would involve:
- Adding new signature types such as hash-based or lattice-based.
- Allowing account-level key rotation.
- Preserving address formats where possible.
- (Might be needed) Coordinating a protocol-level hard fork similar to validator upgrades today.
- If the address format is not preserved, then users need to manually transfer their assets to a new quantum-resistant address format.
Compared to Bitcoin and Ethereum, Solana has superior speed and throughput, enabling a post-quantum migration to happen in hours or days instead of months.
.jpg)
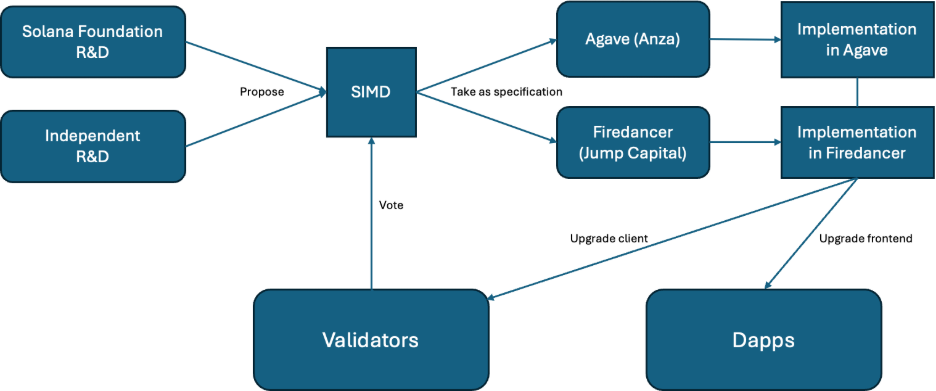
Solana’s ecosystem has repeatedly aligned around complex upgrades, and initiatives such as Alpenglow and Firedancer show a cultural bias toward rapid iteration. This proven ability to reach consensus and implement changes makes Solana one of the most capable L1s to lead a post-quantum migration once standards stabilize.
Moreover, unlike Ethereum and Bitcoin, the Solana signature scheme update might enable users to retain their same front-facing address thanks to a difference between the signature schemes EdDSA (Solana) and ECDSA (Bitcoin, Ethereum). In ECDSA, the private key is used directly to sign messages. In EdDSA, the private key is hashed to a signing key, so in this case, a quantum computer can crack the signing key, but not the private key.
Now, instead of proving “signature corresponds to the public key,” we can switch to a ZK proof showing “User knows a private key, such that after hashing to the signing key producing the valid signature,” which is quantum resistant and keeps the same public key.
Prospects For New Quantum-Proof Chains
While Solana is best positioned among other blockchains like Bitcoin and Ethereum, it’s also important to assess the prospect of new quantum-native chains that will likely arise (and no doubt, make grand promises) if quantum readiness becomes a prominent public investment narrative.
Even if an opportunist chain(s) can capture meaningful attention while the narrative is hot, the odds are against them when it comes to capturing market share from incumbents and achieving staying power.
They’ll still need to attract long-term-committed developers and users, which remains the most difficult challenge for new L1s, taking years to achieve meaningfully. Prior quantum-resistant L1 attempts struggled to build traction because of this. Notable examples were Algorand, Hedera, and QAN.
Instead of new chains surging to dominance, our base case for quantum is that incumbent L1s simply adapt to it and proceed with business as usual. Post-quantum readiness is not a sufficient differentiator for new entrants when incumbents have credible and technically sound migration paths to reach safety.
Conclusion
Quantum computing is a decades-away, long-term risk, and is not an existential threat to Solana.
Despite its lack of urgency, quantum readiness could become a key narrative in 2026. If this occurs, Solana is the best positioned L1 to benefit, as it’s in a better position than other blockchains to transition into a post-quantum future. The network has a live and quantum-safe interim tool through the Winternitz Vault, a favorable migration path enabled by EdDSA, and a proven ability to implement chain upgrades in a timely manner.
And while quantum-native L1s could spring up in an attempt to take advantage of the narrative, we don’t believe they have a meaningful chance of displacing established chains that effectively execute a migration plan.
The real competitive battle for L1s remains what it has always been: winning developer adoption and becoming the default platform for real applications.
Frequently Asked Questions
Is quantum computing an immediate threat to Solana?
No. Breaking today’s cryptographic systems would require thousands of logical qubits and millions of physical qubits with error correction. Current quantum computers are still roughly 150x away from that capability, making “Q-day” a decades-away scenario, not an imminent risk.
How could quantum computers affect crypto wallets?
In theory, advanced quantum machines could reverse-engineer private keys from public keys used in elliptic-curve cryptography. If that happened before post-quantum protections were in place, attackers could potentially steal funds from existing wallets.
What is Solana’s current quantum-resistant solution?
Solana has a temporary mitigation called the Winternitz Vault, which uses hash-based, quantum-resistant signatures. Users can generate a post-quantum keypair offchain and deposit SOL into the vault for long-term quantum-safe storage.
What are the limitations of the Winternitz Vault?
Winternitz signatures require a new address for every transaction, which creates UX and security challenges. Because of this constraint, the vault is considered a temporary solution rather than a permanent fix.
Can developers already build quantum-resistant apps on Solana?
Yes. Developers can build applications using Winternitz signatures, and Blueshift is working on a consumer-facing product that will make this functionality more accessible.
What would a full post-quantum Solana upgrade involve?
A complete migration would likely include new signature types, account-level key rotation, preserved address formats where possible, and potentially a protocol-level hard fork. If address formats change, users may need to manually transfer assets.
Why is Solana better positioned than Bitcoin and Ethereum for post-quantum migration?
Solana’s higher speed and throughput would allow a migration to occur in hours or days rather than months. The ecosystem also has a history of coordinating complex upgrades, such as Alpenglow and Firedancer.
Can Solana keep the same wallet addresses after a quantum upgrade?
Possibly. Because Solana uses EdDSA instead of ECDSA, it may be able to switch to quantum-resistant ZK proofs that verify knowledge of the private key while preserving the same public address format.
Will new quantum-native blockchains replace Solana?
The article argues this is unlikely. Past quantum-resistant L1s like Algorand, Hedera, and QAN struggled to gain traction, and new chains still face the long-term challenge of attracting developers and users.
What’s the long-term outlook for quantum and Solana?
Quantum computing is a long-term risk, not an existential threat. If quantum readiness becomes a major narrative, Solana is well-positioned to adapt thanks to its interim protections, upgrade flexibility, and strong ecosystem coordination.